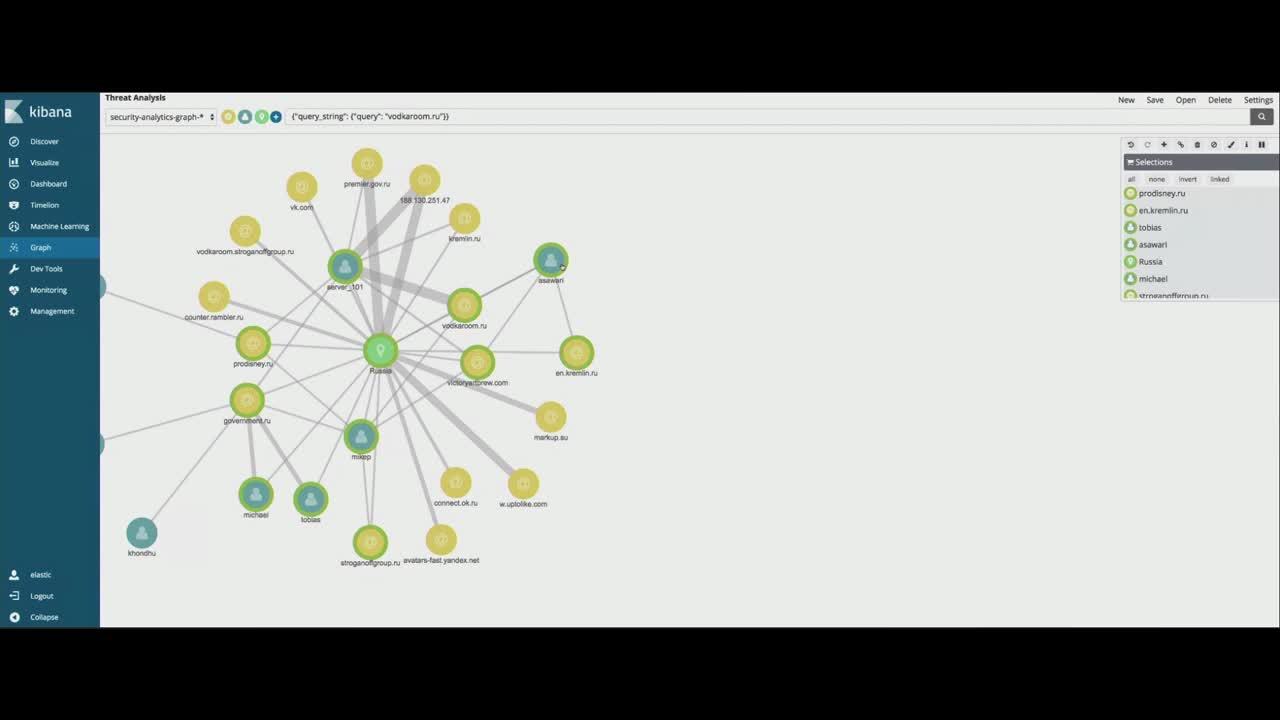
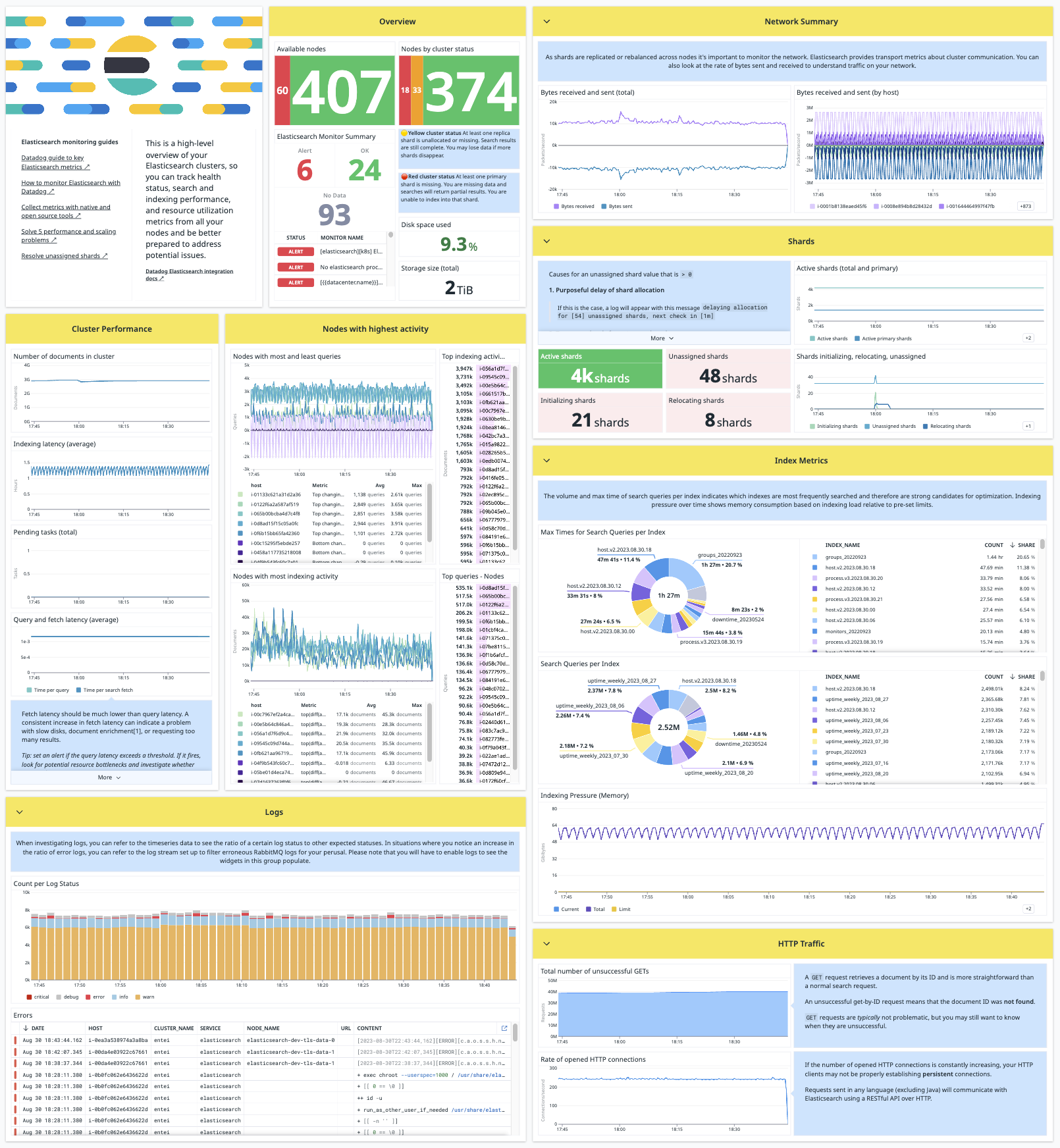
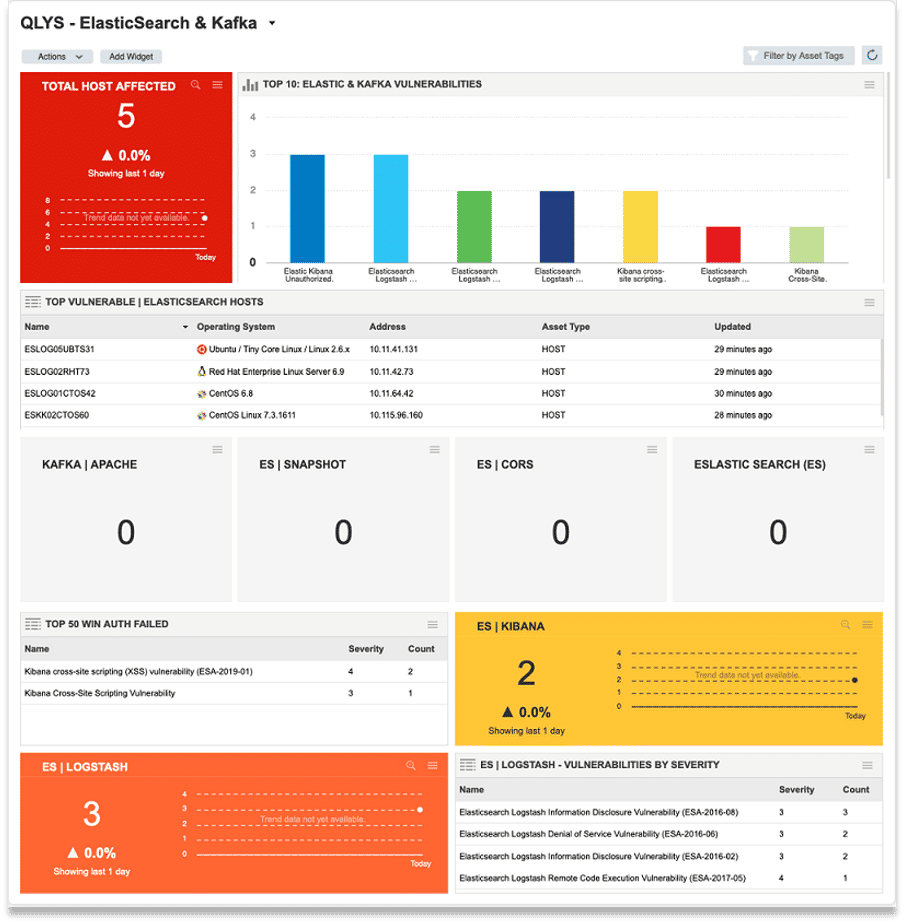
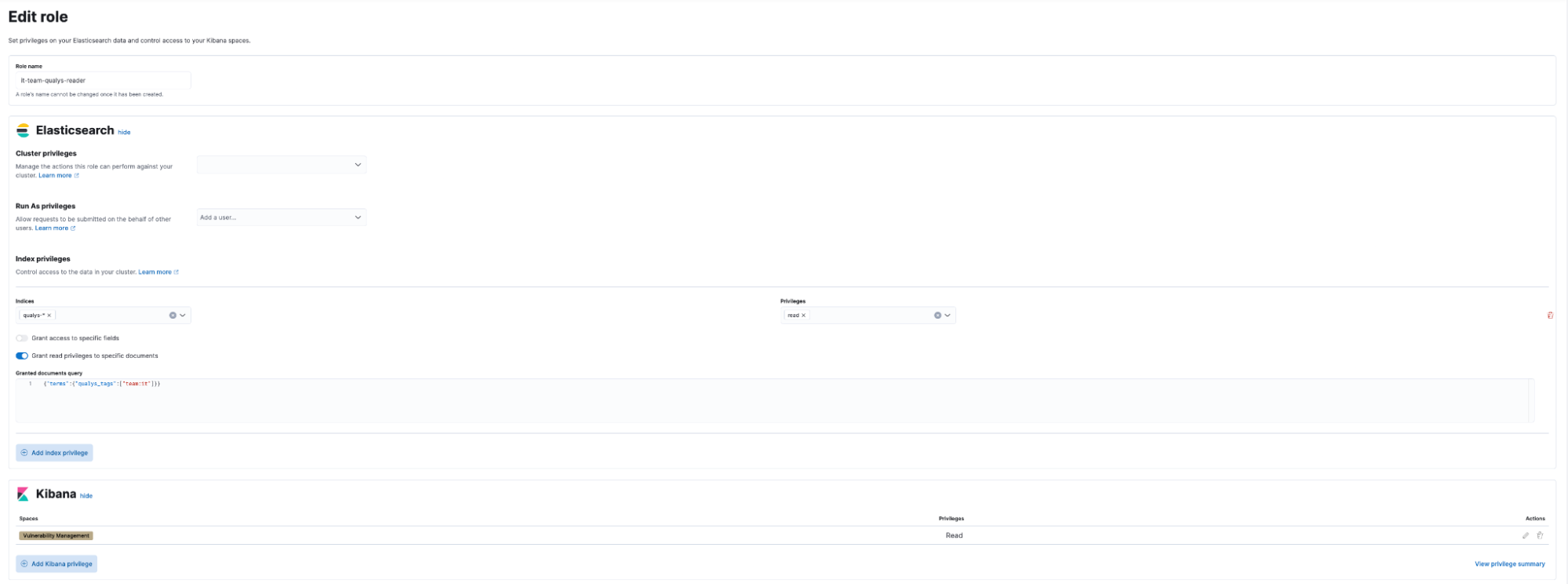
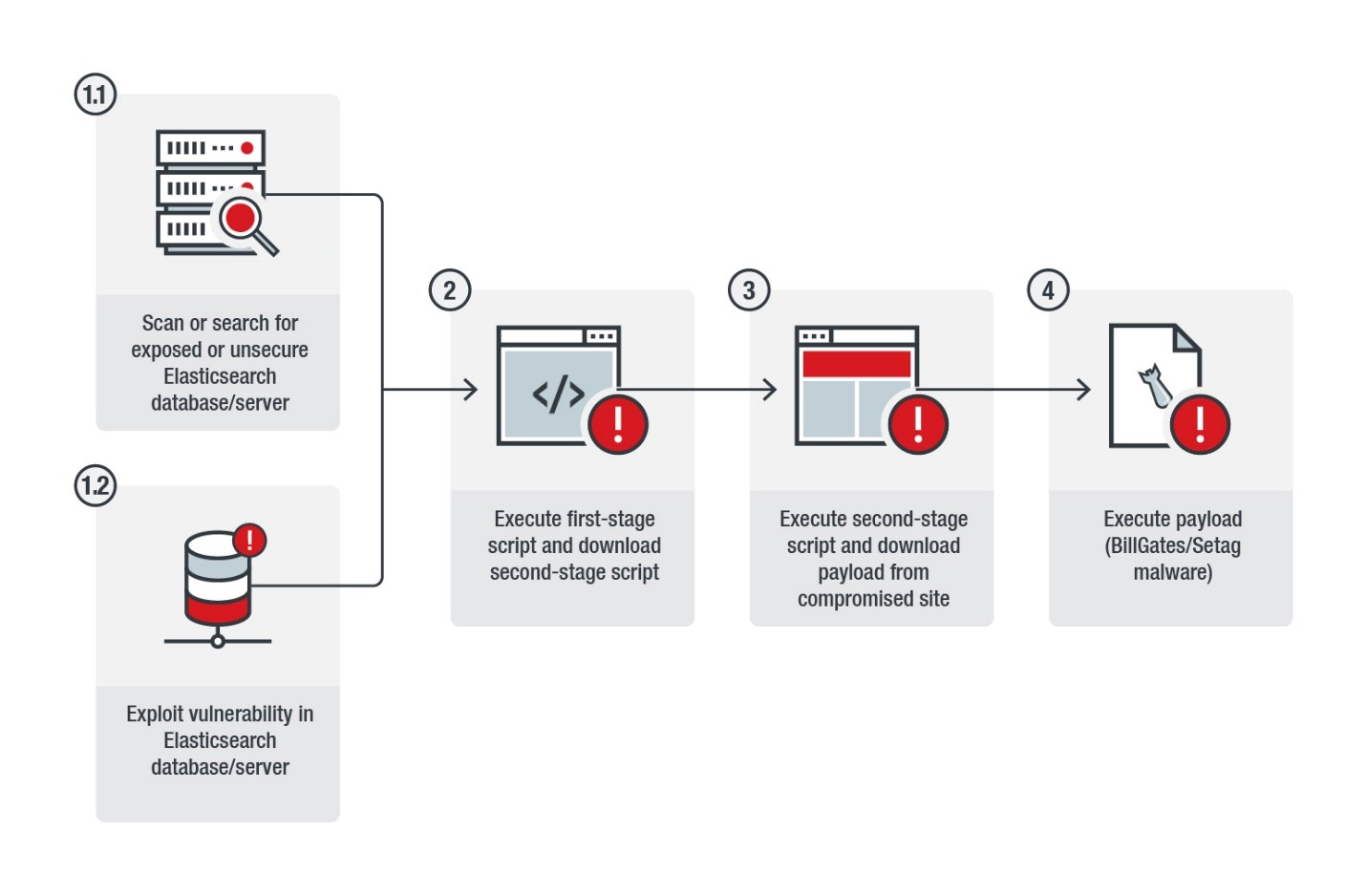
GitHub - HKcyberstark/Vuln_Mod: Vulnerability Assessment Module - OpenVas with Elastic stack using VulnWhisperer
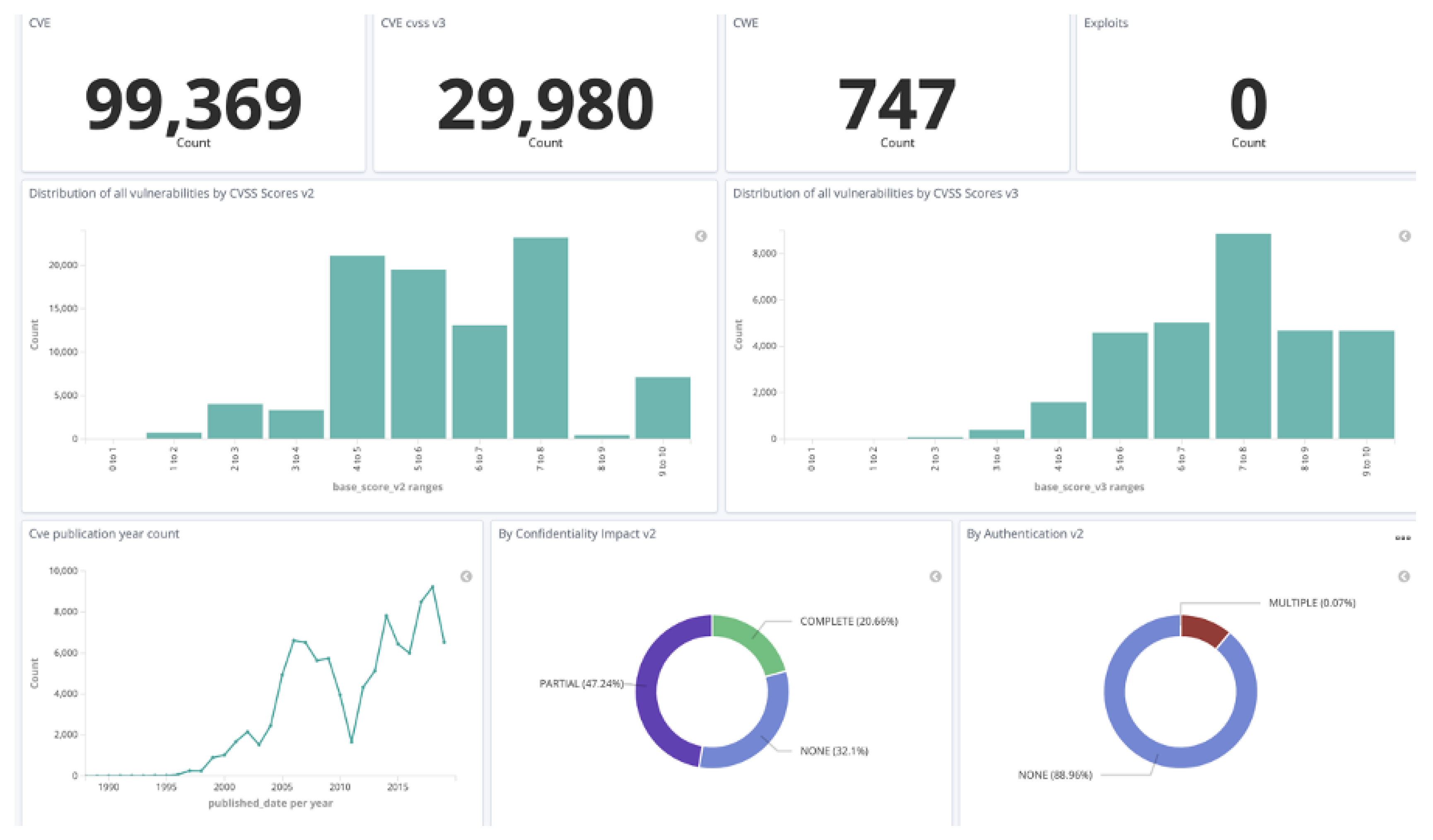
Applied Sciences | Free Full-Text | Efficient Algorithm for Providing Live Vulnerability Assessment in Corporate Network Environment

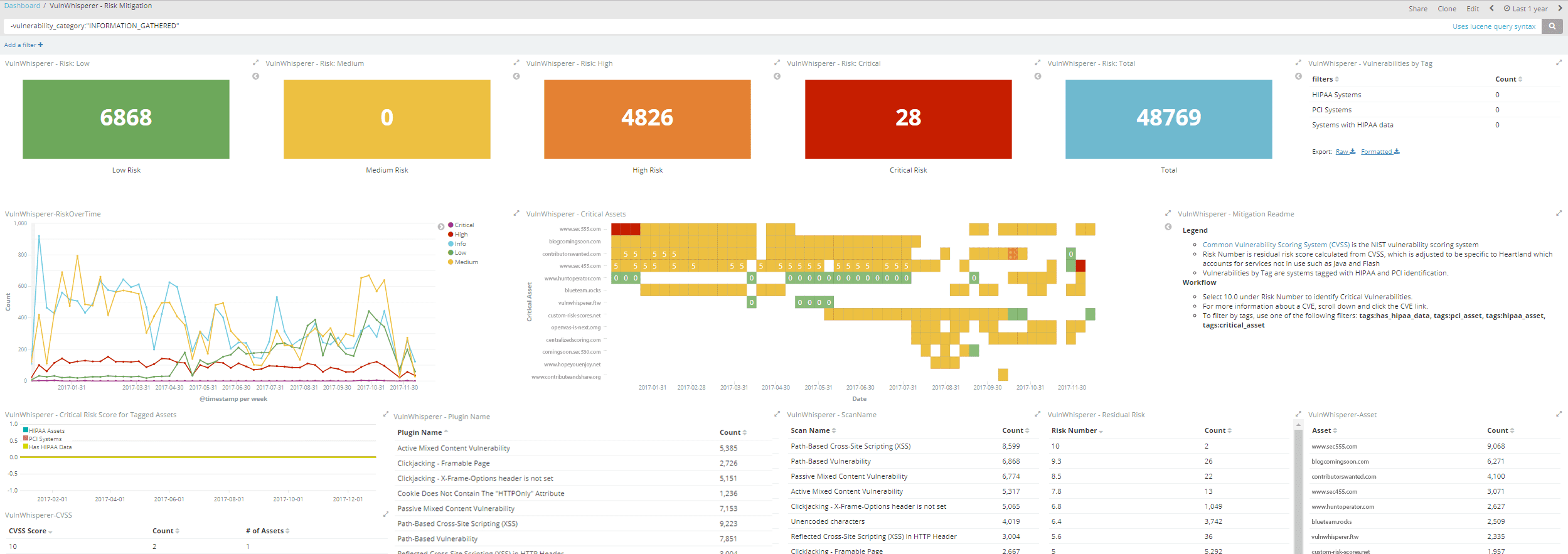

.png)